Generic ClamAV archive evasion
Release mode: Coordinated but limited disclosure.
Ref : TZO-05-2009-ClamAV Evasion
Vendor : http://www.clamav.net & http://www.sourcefire.com/products/clamav
Security notification reaction rating : Good
Affected products :
- ClamAV below 0.95
- Includes MACOSX server,IBM Secure E-mail Express Solution for System and a lots of mail appliances. http://www.clamav.net/about/who-use-clamav/
I used to not report bugs publicly where a a vendor - has not reacted to my notifications - silently patched. I also did not publish low hanging fruits as they make you look silly in the eyes of your peers.
Over the past years I had the chance to audit and test a lot of critical infrastructures that, amongst other things relied on security products (and on security notifications from vendors) and have witnessed various ways of setting up your defenses that make some bugs critical that you'd consider low at first glance, I came to the conclusion that most bugs deserve disclosure.
Please see "Common misconceptions" for more information.
I. Background
Clam AntiVirus is an open source (GPL) anti-virus toolkit for UNIX, designed especially for e-mail scanning on mail gateways. It provides a number of utilities including a flexible and scalable multi-threaded daemon, a command line scanner and advanced tool for automatic database updates. The core of the package is an anti-virus engine available in a form of shared library.
II. Description
The parsing engine can be bypassed by manipulating RAR archive in a "certain way" that the Clamav engine cannot extract the content but the end user is able to. Details are currently witheld (thanks to IBM).
III. Impact
The bug results in denying the engine the possibility to inspect code within the RAR archive. While the impact might be low client-side (as code is inspected upon extraction by the user) the impact for gateways or AV infrastructure where the archive is not extracted is considerable. There is no inspection of the content at all, prior disclosure therefore referred to this class of bugs as Denial of service (you deny the service of the scan engine for that file) however I choose to stick the terms of evasion/bypass, being the primary impact of these types of bugs.
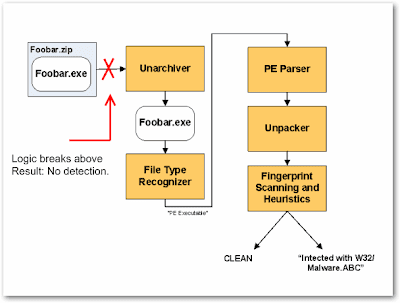
Below is a simplified logic of an Anti-Virus engine (Source: F-Secure - Link), as shown below the logic breaks once the file can't be extracted.
PS. I am aware that there are hundreds of ways to bypass, that however doesn't make it less of a problem. I am waiting for the day where the first worm uses these techniques to stay undetected over a longer period of time, as depending on the evasion a kernel update (engine update) is necessary and sig updates do not suffice. Resulting in longer window of exposure - at least for GW solutions. *Must make confiker reference here*
IV. Common misconceptions about this "bug class"
- This has the same effect as adding a password to a ZIP file
- - This is only an issue with gateway products
- Behavioral analysis will catch this ?
- Evasions are the Cross Site scripting of File formats bugs
IV. Disclosure timeline
IBM was sent two POC files, an explanation and the disclosure terms (http://blog.zoller.lu/2008/09/notification-and-disclosure-policy.html)
- 09/03/2009 : Send proof of concept, description the terms under which I cooperate and the planned disclosure date (23/03/2009)
- 13/03/2009 : Clamav responds that the bug is reproducible and will be fixed in 0.95 to be released the (23/03/2009)
- 23/03/2009 : Ask clamav if the release was made and if credit was given
- 23/03/2009 : Clamav responds that the release was made, and that the credit was given in the changelog. (Tzo note: A post will be probably be made at http://www.clamav.net/category/security/
- 02/04/2009 : Release of this limited detail advisory


.png)

.png)


0 comments
Post a Comment