Release mode: Forced disclosure, no answer from vendor.
Ref : TZO-04-2009-IBM Proventia
WWW : http://blog.zoller.lu/
Vendor : http://www.ibm.com
Security notification reaction rating : Catastrophic (see Timeline)
Affected products : IBM Proventia engine (minimum 4.9.0.0.44 20081231 Official Release) other products using the engine are likely to be affected too. As IBM has not cooperated in any way and I have better things to do than to test IBM products for free I cannot state all affected products, if you are an IBM/ISS customer please call IBM support and request more details.
About this advisory
I used to not report bugs publicly where a vendor either has not reacted to my notifications or silently patched. I also did not publish low hanging fruits as they make you look silly in the eyes of your peers
Over the past years I had the chace to audit and test a lot of critical infrastructures that (also) relied on products (and about security notification from vendors) and have witnessed various ways of setting up your defenses that make some bugs critical that you'd consider low, I came to the conclusion that most bugs deserve disclosure.
Please see "Common misconceptions" for more information.
I. Background
IBM Internet Security Systems (ISS) offers a comprehensive portfolio of IT security products and services for organizations of all sizes.
IBM Proventia Network Mail Security System and IBM Proventia Network Mail Security System Virtual Appliance provide spam control and preemptive protection for your messaging infrastructure.
Proventia Network Mail is the only email security solution equipped with the IBM Intrusion Prevention System (IPS) engine and a behavioral genotype (SIC!) anti-virus technology, along with remote malware detection and Sophos signature-based anti-virus.
II. Description
The parsing engine can be bypassed by manipulating RAR archive in a "certain way" that the IBM engine cannot extract the content but the end user is able to. Details are currently witheld (see below).
A professional reaction to a vulnerability notification is a way to measure the maturity of a vendor in terms of security. IBM is given a grace period of two (2) weeks to reply to my notification. Failure to do so will result in POC being released in two (2) weeks. If IBM is not aware of how to deal with security notifications I recommend them to read my security notification response draft on how to do so at http://blog.zoller.lu/2008/09/notification-and-disclosure-policy.html
As this bug has not been reproduced by the vendor, this advisory relies on the assumption that my tests were conclusive.
III. Impact
The bug results in denying the engine the possibility to inspect code within the RAR archive. While the impact might be low client-side (as code is inspected upon extraction by the user) the impact for gateways or AV infrastructure where the archive is not extracted is considerable. There is no inspection of the content at all, prior disclosure therefore refered to this class of bugs as Denial of service (you deny the service of the scan engine for that file) however I choose to stick the terms of evasion/bypass, being the primary impact of these types of bugs.
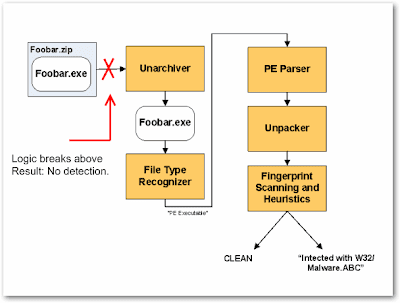
Below is a simplified logic of an AV engines (Source: F-Secure -
Link), as shown below the logic breaks once the file can't be extracted.
PS. I am aware that there are hundreds of ways to bypass, that however doesn't make it less of a problem. I am waiting for the day where the first worm uses these techniques to stay undetected over a longer period of time, as depending on the evasion a kernel update (engine update) is necessary and sig updates do not suffice. Resulting in longer window of exposure - at least for GW solutions. *Must make confiker reference here*
IV. Common misconceptions about this "bug class"
- This has the same effect as adding a password to a ZIP file
The scanner denotes files that are passworded, an example is an E-mail Gatewayscanner that adds "Attachment not scanned" to the subject line or otherwise indicates that the file was not scanned. This is not the case with bypasses, in most cases the engine has not inspected the content at all or has inspected it in a different way. Additionally passworded archive files are easily filterable by a content policy, allowing or denying them.
- - This is only an issue with gateway products
Every environment where the archive is not actively extracted by the end-user is affected. For example, fileservers, databases etc. pp. Over the years I saw the strangest environments that were affected by this type of "bug". My position is that customers deserve better security than this.
- Behavioral analysis will catch this ?
No, the content is unreadable to the AV engine as such no inspection whatsoever is possible.
- Evasions are the Cross Site scripting of File formats bugs
Yes.
IV. Disclosure timeline
IBM was sent two POC files, an explanation and the disclosure terms (http://blog.zoller.lu/2008/09/notification-and-disclosure-policy.html)
- 09/03/2009 : Send proof of concept, description the terms under which I cooperate and the planned disclosure date (23/03/2009) Note: The security contact adress listed in OSVDB was used.
No reply.
- 13/03/2009 : Resend email indicating this is the last attempt to coordinate disclosure
No reply.
- 23/03/2009 : Send another Report and a second POC
No reply.
- 02/04/2009 : Publication of a limited detail advisory, grace period of 2 weeks given to IBM prior to full detail advisory.
- 02/04/2009 : IBM contact is made, proof of concept sent again
- 03/04/2009 : IBM responds that the issue is under investigation


.png)



